It usually starts the same way. CMMC hits the radar, leadership looks around the room, and the assignment lands on the person who manages technology. "This is an IT thing. Can you figure this out?"
The IT leader says yes. That's what good IT leaders do. They start doing what most mid-sized manufacturers do with DIY CMMC. They read,hey pull up NIST 800-171. They call a few vendors. They buy a tool that promises to simplify the process. They build a spreadsheet.
Six months later, the spreadsheet has grown. The progress hasn't.
Month Six Looks the Same as Month Three
The IT director can talk about access controls and encryption with more confidence than they could in January. But the honest update in every leadership meeting sounds the same: "We're making progress, but I'm not sure how far along we are."
It's not that they've done nothing. They've done a lot. The problem is that every answer creates new questions. Access control policies need sign-off from HR. The incident response plan requires coordination across departments that have never coordinated on security before. Physical security controls have nothing to do with anything the IT team manages. Security awareness training needs buy-in from people who report to the COO, not the IT leader.
Meanwhile, the IT team still has their actual jobs. The help desk tickets don't stop because CMMC exists. The network still needs monitoring.
DIY CMMC preparation looks manageable on paper. Six months in, it feels like a second full-time job layered on top of the first one, with no way to measure whether the work is actually moving toward certification.
Five Out of Fourteen
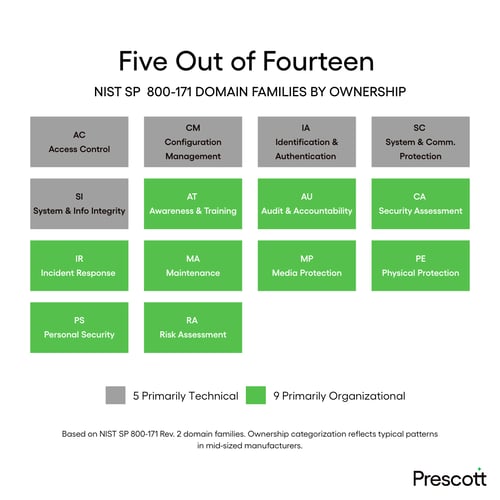
At some point, the IT leader sits down with the NIST SP 800-171 requirements and maps what they've built against the fourteen domains. The technical side looks solid. Network security, system hardening, access controls. The team knows that work.
-
Then they hit personnel security. That's HR policies and background check procedures. Not their department.
-
Physical protection. Facility access controls and visitor logs. Not their building to manage.
-
Awareness and training. A company-wide program with tracked completion, owned by people who don't report to them.
-
Risk assessment needs leadership involvement and documented business impact analysis.
-
Incident response needs a cross-departmental plan nobody has written.
-
Audit and accountability needs log review processes with roles that don't exist yet.
Out of fourteen domains, the IT team can own maybe five. The rest require decisions, budget, and authority that sit outside their role entirely. They've been identifying organizational problems for months with no organizational mandate to solve them.
That's the week the IT leader stops being behind on a project and starts carrying one they were never equipped to finish.
It Was Never an IT Project
Nobody pulls up the CMMC framework and looks at its full scope before handing it to IT. Nobody counts fourteen domains and asks how many of them are actually technology decisions.
Every article frames DIY CMMC as a technology project. Every vendor pitch is about tools and controls. Every webinar walks through technical requirements and assumes the IT team will handle the rest.
The IT leader didn't fail. They were sent into unfamiliar territory with a map drawn by people who only see the technical layer. They covered the ground they could see and flagged the territory they couldn't reach. That's exactly what a capable person does with an incomplete map.
The question isn't whether the team is good enough. It's whether anyone told them this was a fourteen-domain organizational change project before they said yes.
The Work Isn't Wrong. It's Disconnected
The IT leader's technical work has value. They know the environment better than any outside expert ever will. What's been missing is the compliance picture laid over the technical picture, so the controls they built connect to what an assessor actually evaluates.
When that picture exists, everything moves differently. Controls already in place get documented properly. Gaps that were invisible become visible and prioritized. Work that sits outside IT gets assigned to the people who should own it. And the IT leader stops carrying a project alone that was never one person's job.
A gap assessment is often the turning point where DIY CMMC efforts stop spinning and start connecting to certification. It shows where the team actually stands, which domains are covered, and where the gaps live. Contact Prescott to start that conversation.
Frequently Asked Questions
They can handle parts of it. Most IT teams are well-equipped for the technical controls: access management, system hardening, encryption, and network security. The challenge is scope. CMMC Level 2 draws from NIST SP 800-171, which spans fourteen requirement domains. In most mid-sized manufacturers, the IT team can directly own the domains that are primarily technical. But domains like personnel security, physical protection, risk assessment, incident response, and security awareness training require coordination, policy creation, and ownership across departments that IT doesn't control. IT teams typically get stuck not because they lack skill, but because they've been given an organizational change project with authority over only part of the scope.
They solve different problems. A managed service provider manages the technology environment. They handle infrastructure, monitoring, patching, and day-to-day IT operations. A compliance consultant addresses the organizational, policy, and process requirements that sit outside the technology layer. CMMC certification requires documented policies, cross-departmental coordination, risk assessment frameworks, training programs, and evidence that controls are implemented and sustained. An MSP can support the technical controls. A compliance consultant maps the full scope of what an assessor evaluates and ensures every domain has an owner, not just the ones IT manages.
Most mid-sized organizations need 9 to 12 months for sustainable preparation. The timeline depends less on the assessment itself and more on where the organization is starting. Companies with existing security practices and some documentation in place move faster. Companies starting from limited cybersecurity maturity may need longer to build policies, train personnel, implement controls, and create the documentation an assessor requires. Industry estimates range from 6 to 18 months depending on organizational size and baseline security posture. Rushing the process increases the risk of a failed first assessment, which adds cost and delays certification further.
A gap assessment is a structured review of an organization's current security posture against all applicable CMMC controls. It evaluates what's already in place, identifies where gaps exist, and produces a prioritized roadmap for closing those gaps. The assessment covers all fourteen NIST SP 800-171 domains, not just the technical ones. That includes reviewing policies, documentation, training records, physical security procedures, incident response plans, and organizational processes. The result tells leadership and IT exactly where they stand, which controls are met, which need work, and which domains need ownership assigned outside the IT department.
They stall because CMMC is framed as a technology project but structured as an organizational change initiative. IT teams start strong on the technical controls they know: access management, encryption, network security. Progress is visible early. Then they hit the domains that require HR policies, physical security controls, cross-departmental incident response plans, leadership-driven risk assessments, and company-wide training programs. These aren't IT decisions. They require budget, authority, and coordination the IT team doesn't have. The project doesn't fail dramatically. It stalls quietly. Updates get vaguer, timelines stretch, and the gap between effort and certification progress widens. The work the IT team has done usually has value. It just needs connecting to the full compliance picture so every domain has an owner and every control maps to what an assessor evaluates.


